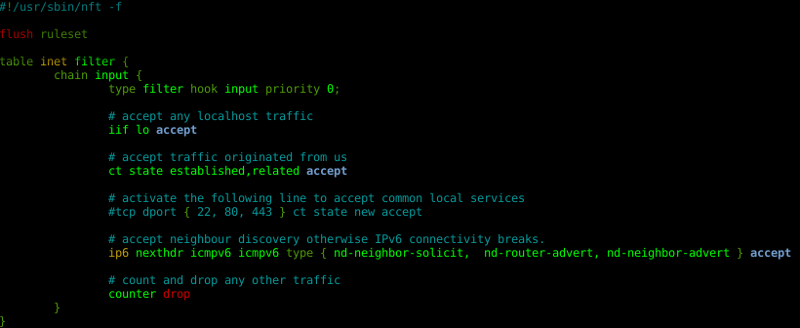
Debian Nft Show Rules
Continue the ruleset evaluation with the next rule. The linux kernel subsystem is known as nf_tables, and 'nf' stands for netfilter.
Ip daddr 8.8.8.8 counter packets 0 bytes 0.

Debian nft show rules. % nft list chain filter ouput table ip filter { chain output { type filter hook output priority 0; This file will be read when nftables starts. } # allow lan to firewall, disallow wan to firewall chain input { type filter hook input priority 0;
But when i reboot my nftables rules and tables dissapiered! If nftables is blocking some services, enable the log. Step one — migrate your iptables rules to nftables rules.
You might need to add additional “forward” policies for docker. Command not found garry@debian:~$ man nft garry@debian:~$. See my example nftables.conf file.
You can list the rules that are contained by a table with the following command: We can insert rule with handle number; Return from the current chain and continue at the next rule of the last chain.
Iifname lan0 accept iifname wan0 drop } # allow packets from lan to wan, and wan to lan if lan initiated the. List rules with handle number: Drop the packet and stop the remain rules evaluation.
Be sure the result is inserted before the drop rule. Sudo nft add rule inet example_table example_chain tcp dport 22 counter accept here, the tcp dport 22 portion contains the rule’s two expressions. If the containers are not on the default docker network, there's no rule allowing them to reach the host.
On debian the nftables configuration file is: Try adding a rule for testing this. Sudo nft list ruleset > /etc/nftables.conf.
Add corresponding rules based on the content of the log: Nft (8) nft (8) name. Ensure your rules are stored in /etc/nftables.conf.
Nft rules would auto restore nftables rules when operation system restart, or manual to exec following command: Root@host:~# nft replace rule ip filter input handle 38 iifname eth0 ip saddr 192.168.1.12 counter drop insert. Queue the packet to userspace and stop the remain rules evaluation.
And it was saved right in place/. , if the manual is not there, then you need to install nftables. Define wan = enp3s0 define vpn = wg0 define vpn_net = 10.10.10.0/24 # setting up a table, simple firewalls will only need.
This rule takes packets from the example_chain and allows those representing tcp traffic on port 22: Flush ruleset # defining variables is easy in nftables scripts. How to config for persistent nft rules.
To create a rule, use a command similar to the example. For example, but your output may be different: Please replace ens33 to interface name of your device.
You can also list rules by chain, for example: Nft is the command line tool used to set up, maintain and inspect packet filtering and classification rules in the linux kernel, in the nftables framework. We can replace rule with handle number list rules with handle number:
Accept the packet and stop the remain rules evaluation. In a base chain it is equivalent to. It matches tcp packets and then matches when those.
How To Drop A Packet In Linux Iptables Ebtables Nftables And More - Codilime
Iptables Vs Nftables Whats The Difference

Securing Your Server With Nftables Datapacketcom
New In Debian Stable Stretch Nftables

Additional Filters Via Nftables
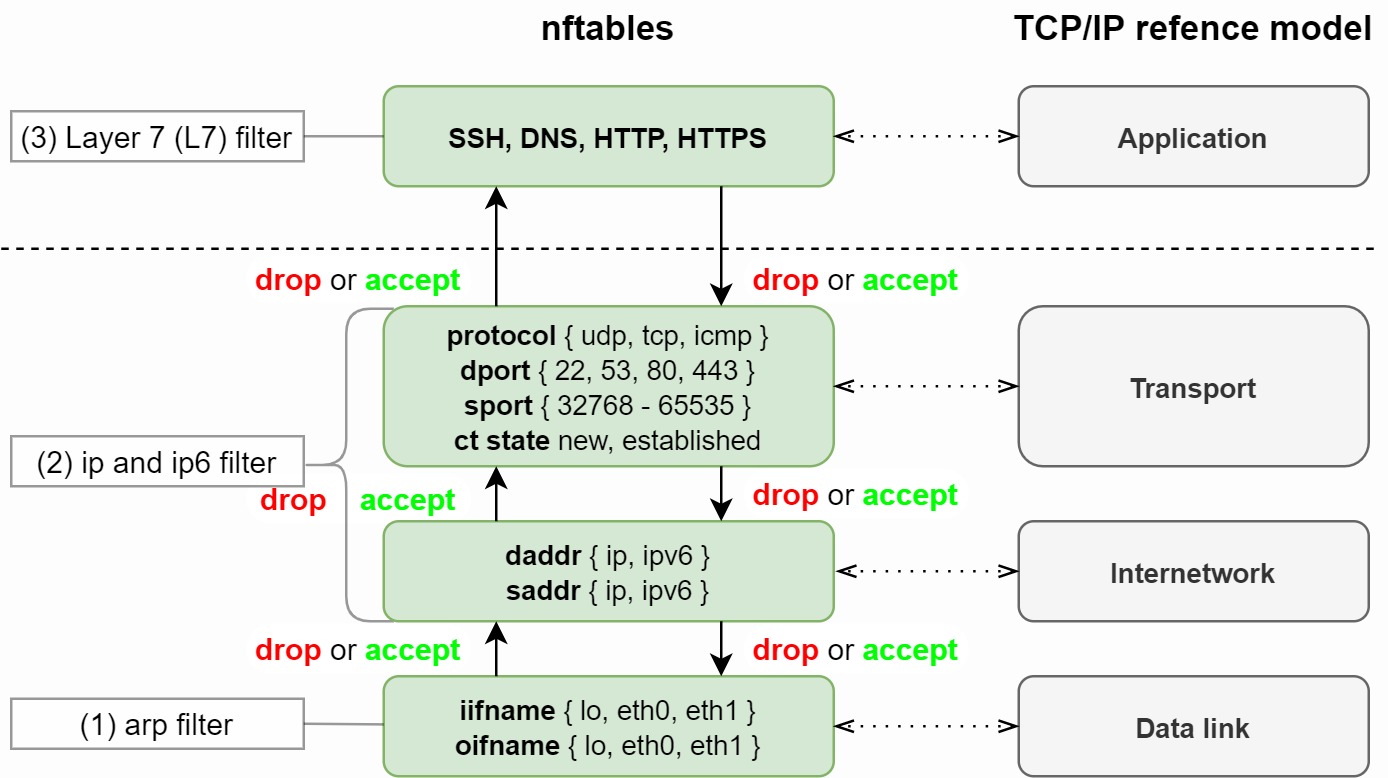
Setting Up Nftables Firewall Cryptsus Blog

Nftables Configure That Linux Firewall Like An Expert

How To Install Nftables In Ubuntu - Liquid Web

Using Nftables On Oracle Linux 8 - Youtube

Beginners Guide To Nftables Traffic Filtering - Linux Audit

Additional Filters Via Nftables
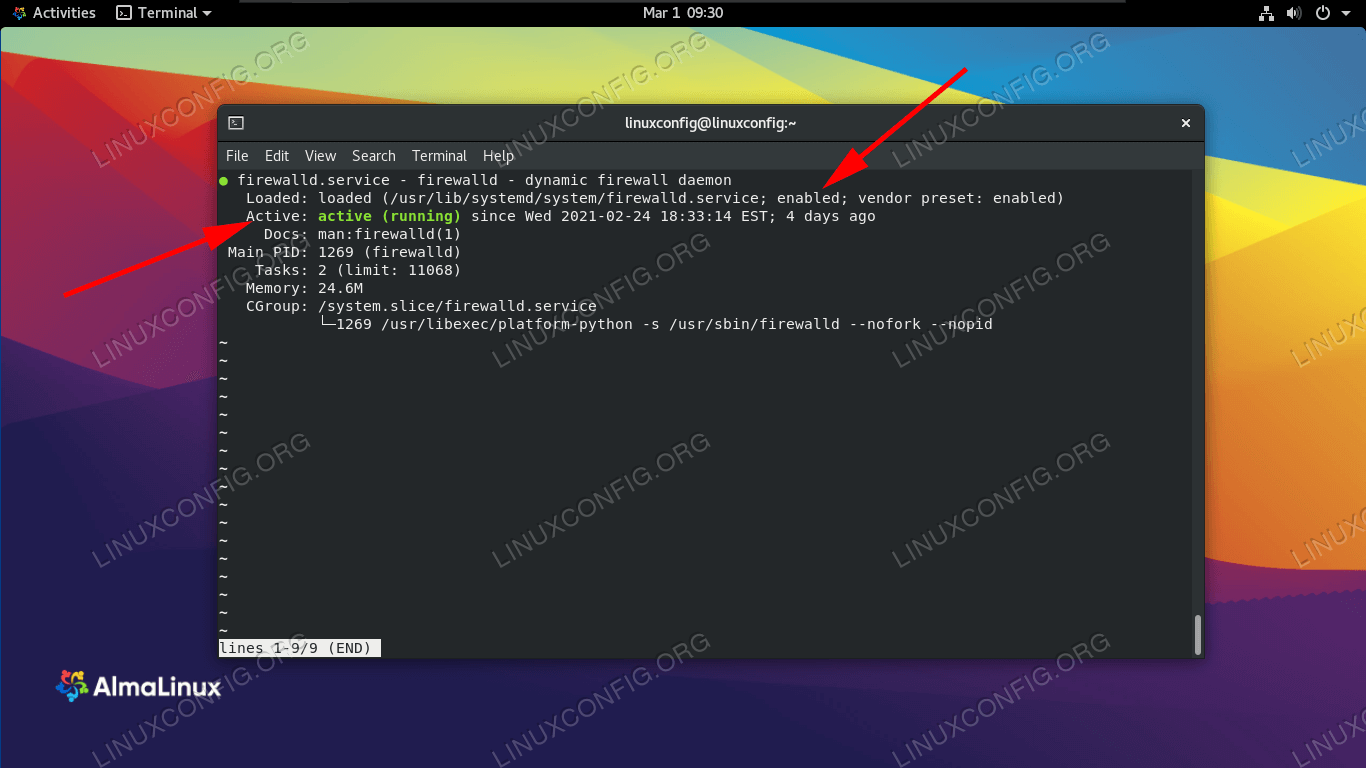
How To Disableenable Firewall On Almalinux - Linux Tutorials - Learn Linux Configuration

Firewall Archives - Linux Tutorials - Learn Linux Configuration
Optimizing Iptables-nft Large Ruleset Performance In User Space Red Hat Developer

How To Install And Configure Squid Proxy On Debian 10 Linux Linuxize

Beginners Guide To Nftables Traffic Filtering - Linux Audit
How To Install Nftables In Ubuntu - Liquid Web